Search results for: 'the graph of two functions (f g)(2)'
- Related search terms
- The Microarchitectural Data Sampling (MDS) vulnerabilities are a set of weaknesses in Intel x86 microprocessors that use hyper-t
- the plant shack e email address
- THE GOOD DOCTOR torrent
- The observer's brain is very sensitive to ratios in images. Good makeup shifts the observed ratios to ranges the brain has been
- The recipient's mailbox is full and can't accept messages now. Please try resending your message later, or contact the recipient
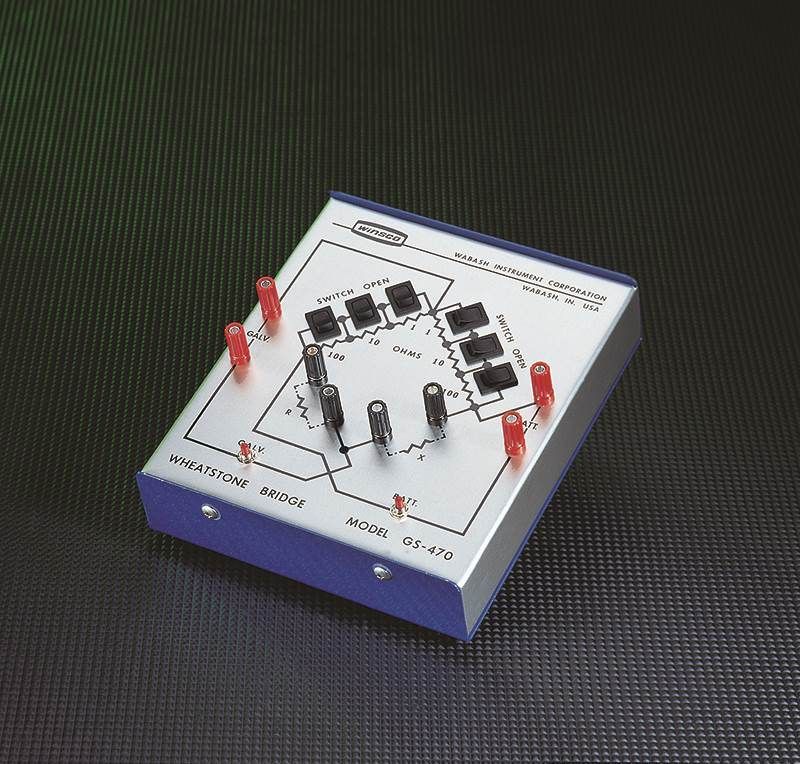
- Bridge, Wheatstone, Diamond Form$395.00
- Archimides Principle Tube$31.50
- Photogate$137.50
- Wheel and Axle, Elementary$15.00
- Second Law of Motion$92.50
- Convection and Ventilation Box$103.43
- Kilovolt Power Supply, Daedalon®$916.32
- Transformer Wc278$132.83
- Universal Power Supply, Daedalon®$1,215.95

 Biology
Biology Chemistry
Chemistry Earth Science
Earth Science Labware
Labware Physics
Physics Wildco Environmental Sampling
Wildco Environmental Sampling